
Cyber Security And What We Should Do In 2020
Ask any expert in IT security and you will get the same response. One of the biggest obstacles to cybersecurity is the human element, which makes knowledge of cybersecurity more important than ever in our mobilized, advanced society.
When the year comes to a close, each of us in the information security industry will stop worrying about what we learned in 2019 and take a moment to focus on. Then, with that in mind, we will be moving forward and looking hard at what we want to see in 2020.
Cybersecurity is a constantly changing game of wits where hackers and defenders tend to overstretch each other. Staying up-to - date with the latest cybersecurity developments is not only beneficial; it is crucial for those concerned.
Large-scale violations of data still make it to the headlines – including attacks by Facebook, Toyota, Microsoft and the American Medical Collection Agency this year. Yet the attacks are less targeted-with hackers specifically targeting more small businesses and customers. Last year saw a 50 per cent rise in the number of data theft from four years earlier. TechRepublic states that this year alone, more than 3,800 data breaches hit organisations.
Attacks are growing not only in numbers but in efficiency as well. Cyber threats are becoming more frequent and complex with technology becoming more advanced and disruption occurring at every turn.
You should be aware of the following cyber-security developments by 2020:
Cybersecurity investment will increase further
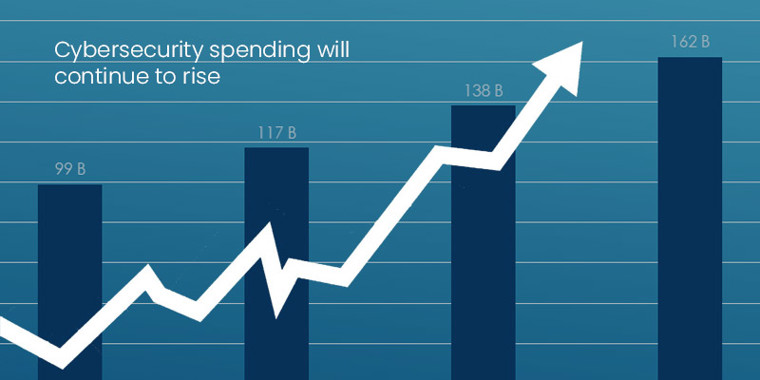
Global security expense is forecast to reach $128 billion by 2020. Nevertheless, the 2019 Global Endpoint Security Trends Report published by Absolute shows that increased spending alone can not ensure better security. The report notes that 70 percent of the breaches came from it, despite 24 percent of total cybersecurity spending going to endpoint security. In endpoint device procedures the false sense of security and complacency led to more holes and vulnerabilities
Then, focus on getting the company organized and updated. The skills gap in cybersecurity remains the way it was 3 years ago. Dark Reading highlights that there is a shortage of cybersecurity workers in around three quarters of organisations.
However, a Burning Glass Technologies report states that the increase in job posts addressing cybersecurity-related skills has far outpaced the growth in graduate numbers.
That's despite a lot of people studying the many forms of cyber security. Udemy currently has over 926,000 students studying cybersecurity courses which is a clear indication of knowledge demand. Organizations need to invest more in systems on risk assessment that concentrate on knowledge transfer and skill development.
Evolving Phishing World

Hackers are creating ever more advanced phishing techniques, pretending to deceive users as respectable organizations or recognizable persons. Email will tend to thrive as the most common form of phishing, but mobile threats are on the rise and phishing attacks happen via sms (smishing) and over the phone (vishing).
Although phishing isn't new, intensity of these types of cyber breaches is rising. According to a survey by AIG, Phishing has topped ransomware as the top cyber insurance claim, responsible for roughly a quarter of all claims.
BYOD Boosts workplace, but at a high price

Further workspaces allow the use of personal devices for work, provide remote work flexibility, improve efficiency and lower costs. Yet bring-your-own-device (BYOD) includes increased risk of data leakage, malware infection, and vulnerability disclosure due to lack of system integration.
To keep up with this cybersecurity trend, technology administrators are now under the pressure of additional IT infrastructure. BYOD certainly won't go away any time soon, but the cyber risks will continue to increase. The development of BYOD policy processes and protocols will help find a happy medium between risk and reward.
More CISOs Take a seat at the table

Of all developments in cybersecurity, this one might just be our personal fave. While we've seen an increase in the popularity of the CISO in the last few years , the amount of CISOs in the boardroom is finally catching up. CISO's stronger relationship with the official forms of cybersecurity is at the center of the board agenda.
Growing protection and privacy issues stem regulatory pressure

The last few years have seen a sharp increase in security and privacy regulations and there are no signs of slowing down this development. Grey areas in enforcement are driving the demand for more regulation – from both consumer and business.
In reality, US technology firms from the Business Roundtable wrote a statement urging congress to formulate a complete consumer data privacy law. The letter was signed by 51 CEOs from major tech companies including Amazon, IBM, and Salesforce. It shows that consumer trust is becoming a concern following large scale data violations.
Surge in attacks by Ransomware targeting local governments

More than 55 cities and towns have been infected with ransomware so far this year. These attacks strain budgets of local governments responsible for social facilities and may cripple such agencies and municipal bodies. Such events highlight the need for local governments to invest in technology with the same urgent strategy as private sector investors.
Cybersecurity Automation Strengthen the efficiency of security staff

Automation moves in to give cybersecurity a hand. Automation has been found to increase productive capacity and increase the ability to manage vulnerabilities at higher speeds in a sector plagued by high turnover rates and a lack of expertise. Automation can never replace human workers, but it can add another security layer and prevent failures.
Mobile vectors are becoming more common

When more companies and customers rely heavily on their cell phones, this weakness is increasingly being exploited by hackers who target apps. Falsified mobile purchases and fake smartphone applications are on the rise next year. Additionally, as the Internet of Things becomes an integral part of industries, multi-endpoint attacks will become more prevalent in 2020.
Security knowledge should remain important in patching organizations vulnerabilities. Developing a culture geared to protection and inspiring workers against attackers will boost innovation against cyber attacks dramatically.
Cyber Warfare Threats Increase

At a global scale, with state-sponsored cyber warfare attacks that can invade electricity grids and nuclear programmes, DDoS attacks that can disrupt public infrastructure, and social manipulation attacks that can be used to hack networks and spread disinformation, we are seeing a increasing challenge to nations and their cultures and societies.
Another aspect of cyber warfare that is especially concerned is that it may become difficult to trace the origins of the attack and decide if the perpetrators are either state-sponsored or lone actors.
AI Swiftly Becoming a Double-Edged Sword

The development in cybersecurity is fast to take the industry by storm. Artificial Intelligence ( AI) has tremendous benefits , particularly in cybersecurity. Yes, 61 per cent of companies claim they can't detect attempts at violations today by using AI. Yet what will keep malicious actors from reaping the benefits of this disruptive technology as AI becomes central to cybersecurity? Cyber attacks are actually crippling, with security departments being overwhelmed, understaffed, and underqualified. We might see cyber attacks like spear phishing and ransomware on a much larger scale with AI and machine learning which is difficult to handle.
Strict Cloud Security Measures Lead to End-User Trust

Confidence is growing in cloud computing. While major data breaches in 2018 and 2019 were triggered by poorly configured cloud security mechanisms, most importantly the recent data breach in Capital One, cloud providers are more frequently enforcing tighter security controls and reviewing security features, leading to reports of improved end-user trust.
Focus Shifts to Third Party Vendor Security

Using a solid cybersecurity policy is no longer enough; third-party suppliers also need to be tested diligently. Yet managing risk from third-party vendors has proven to be a challenge. Hackers are using smaller third-party vendors as an approach to bigger businesses. In fact, 69 per cent of organizations reported a violation resulting from vendor access.
What’s not changing?

Human error and incompetence of staff are still the principal causes of data breaches
Human error goes on pushing data breach record numbers. That's the greatest threats to cybersecurity are inside your business. Training has the potential to reduce risk. Employees will go from being the weakest link in their protection to being the human shield for your company through cyber literacy training.
The skills deficit issue persists hanging over the industry
According to the Cyber Security Employment Survey, there will be 3.5 million unfilled cybersecurity vacancies worldwide by 2021, with an unemployment rate in cybersecurity at 0 percent. The impact of this skills shortage on the industry has been severe, leaving divisions of security exhausted, under-trained and under high stress.
Don't wait until NCSAM arrives before considering updating your plan on cybersecurity. As these outlined developments see broader acceptance, the cybersecurity environment possesses the potential for dramatic change. Cyber crimes as they stand, differ in scope and severity, making it impossible to keep up. But having those patterns on your radar going into 2020 is key to ensuring that you remain safe.
Last but definitely not least ...
Cybercrimes are becoming more prevalent and dangerous. Cybersecurity can no longer be put on the backburner as the world becomes increasingly digitised. National Cybersecurity Awareness Month (NCSAM) is held every October to raise awareness of the growing concerns about the digital world's safety and security.
We also have no hindsight advantage to show just what security risks we will face in 2020. The hyper-connected world today provides more opportunities for cyber criminals and through the IT ecosystem is a potential target: on-premise networks, cloud, mobile devices, and IoT devices. But it's forewarned: using advanced intelligence threat to drive centralized security infrastructure, companies of all sizes will automatically defend themselves from coming attacks.
Royex Technologies is a leading mobile application development and web development company in Dubai. Our excellent founding team are determined to achieve solid growth in the web solution market. So if you are thinking to develop an app/ website/ ecommerce website, you can directly call at this number : +971566027916





